November 27, 2018
Sponsored by Webroot
Each year, Webroot publishes an addendum to its annual threat report where we parse data from January through June to see what insights we’re able to glean from the first half of the year. This approach provides us with a head start on piecing together cyber storylines from across the web and helps our threat researchers begin to understand which threats will define the year.
The 2018 Webroot Threat Report Mid-Year Update features some notable findings. While
Here’s a rundown of some interesting findings, but be sure to download your complete copy for full details.
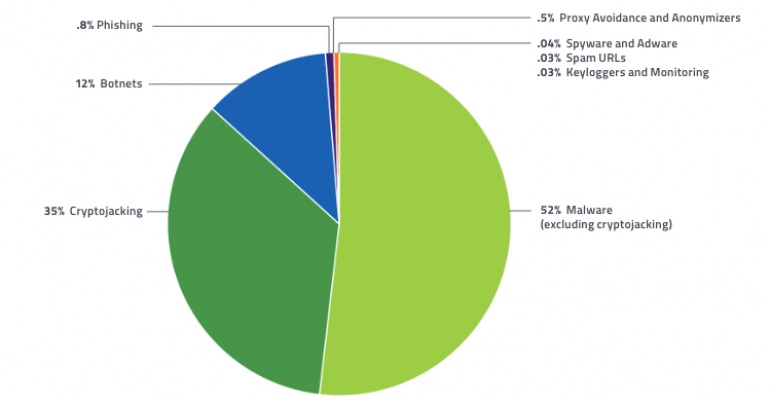
Malware Loses Steam
Malware continues to reign in terms of sheer threat volume. Of the malicious traffic Webroot monitored in the first half of the year, 52% was malware. But it’s losing significant steam. Webroot researchers recorded a 50% drop in malware traffic compared to the same period one year prior.
The reason? Cybercriminals are always experimenting with less labor-intensive ways to scam their victims. From the report:
“This 50% drop is largely because there are easier ways to profit from remote systems than by deploying malware. It only takes a small number of people to view a website that hosts cryptojacking JavaScript for a bad actor to not just break-even but make a quick profit.”
Botnets, especially those that deliver banking Trojans like Emotet and Zeus Panda, remain a concern. Both were included in our list of this year’s nastiest malware.
Ransomware’s New Business Model
Last year’s top threat has come a long way since the days of holding files hostage for Bitcoin. This is largely due to rising awareness of the threat. That’s led IT teams to backup data more regularly. And, as with malware, easier methods for moneymaking surged in popularity in early 2018, hastening ransomware’s gradual decline.
But ransomware has not gone away. It’s only gotten more targeted. Again from our report:
“[It] has become a more targeted business model for criminals who seek out unsecured Remote Desktop Protocol (RDP) connections as the attack vector. Using tools like Shodan, malicious actors scan for the many organizations that have left their environment wide open to infiltration by not creating adequate RDP settings.”
Once they’ve gained access through an unsecured RDP, cybercriminals can demand ransoms in the form of cryptocurrencies, disable endpoint security or simply conduct reconnaissance on the value of the data to which they now have access.
The Surging Threat of Cryptojacking
There’s a new top dog roaming the cyber threat landscape. The use of cryptojacking, the process of surreptitiously hijacking a machine’s computing power and redirecting it to mine cryptocurrencies, has skyrocketed since the beginning of 2018.
Our report details the scope of the issue:
“[It] may be largely invisible to the end user, who likely won’t notice a small spike in their electric bill. But for an organization, power bills can skyrocket, especially when criminals employ scaling, i.e., keeping the drain on the CPU minimal when a keyboard or mouse is being used but scaling up to 100% at other times.”
To get a sense of just how large a problem this has the potential to become, Webroot estimates that, with energy use for mining doubling every six months, it could account for as much as 3% of the world’s electricity consumption by 2020.
Layering Security to Protect Against Threats
The cybersecurity threat landscape changes rapidly enough to warrant mid-year updates to our annual threat report. And, at Webroot, we believe it shifts quickly enough, and in such unpredictable ways, that simply protecting endpoints is no longer enough. Users and networks require protection, too.
To learn more about how to protect your clients against all the year’s top threats with layered solutions at the endpoint, network and user levels, contact us.
This guest blog is part of a Channel Futures sponsorship.
You May Also Like
